BSI IT-Grundschutz: A Step-by-Step Guide for IT Security Compliance

IT security compliance is no longer a luxury for modern organizations; it’s a necessity. For companies in sectors with critical infrastructure or sensitive data, the stakes are even higher. With threats evolving daily, robust frameworks like BSI IT-Grundschutz are essential tools for ensuring your systems are protected and meet regulatory requirements.
But what exactly is BSI IT-Grundschutz, and how can your organization use it to strengthen IT security? This guide will walk you through everything you need to know, from its purpose to implementation steps, so you can achieve compliance and secure your digital environment effectively.
What is BSI IT-Grundschutz?
BSI IT-Grundschutz is an IT security framework developed by the German Federal Office for Information Security (Bundesamt für Sicherheit in der Informationstechnik, or BSI). It provides a structured approach to achieving IT security by combining best practices, risk management, and targeted controls. The framework acts as a practical guide for organizations to establish effective security protocols while remaining compliant with legislation like the General Data Protection Regulation (GDPR).
Why is BSI IT-Grundschutz Important?
BSI IT-Grundschutz offers several advantages:
- Comprehensive Coverage: It addresses technical, organizational, and human factors, offering a holistic approach to IT security.
- Scalability: Suitable for both small businesses and public institutions with complex infrastructures.
- Compliance-Friendly: Helps organizations adhere to national and international IT security standards.
- Risk Management: With its structured methodology, the framework aids in identifying and mitigating risks effectively.
Who Should Implement BSI IT-Grundschutz?
This framework is ideal for:
- Government and Military agencies aiming to protect sensitive information.
- Critical Infrastructure (KRITIS) entities, where system failures could have severe consequences.
- IT/OT Consulting Firms helping clients audit and improve their cybersecurity posture.
- Cybersecurity Students looking to gain a deeper understanding of global security frameworks.
- IT Professionals and Security Consultants tackling risk management and compliance for their enterprises.
If you belong to any of the categories above, BSI IT-Grundschutz could play a vital role in your security strategy.
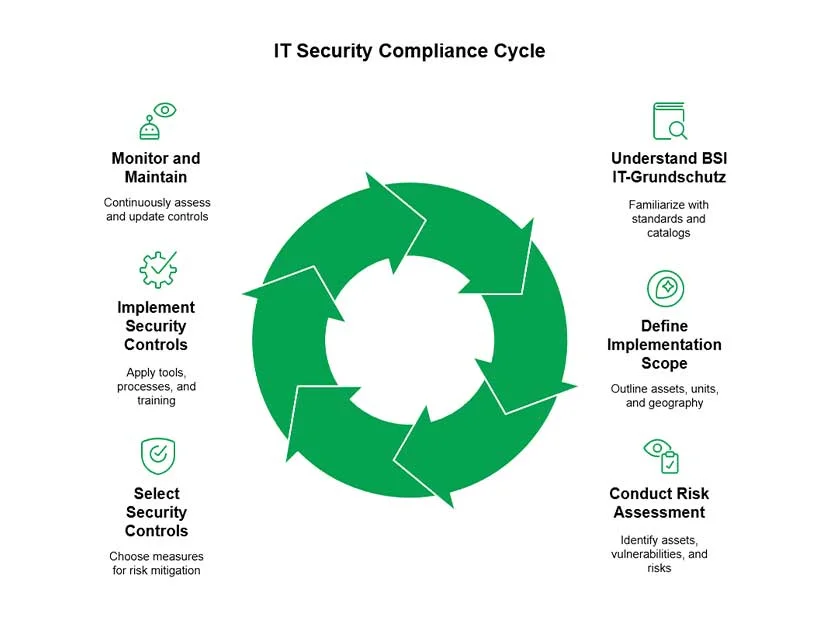
Step-By-Step Guide to IT Security Compliance
Successfully implementing BSI IT-Grundschutz doesn’t have to be intimidating. Here’s a detailed breakdown of the process:
Step 1: Understand the Basics of BSI IT-Grundschutz
Before you can secure your organization, it’s important to familiarize yourself with the framework’s structure. BSI IT-Grundschutz provides two essential components:
- Standards (e.g., ISO/IEC 27001): These form the foundation of your security management system.
- IT-Grundschutz Catalogs (Modules): These detail recommended security practices for various organizational areas (e.g., servers, networks, personnel).
Beginnen Sie damit, diese Dokumente sorgfältig zu prüfen. Achten Sie auf Abschnitte, die für Ihre Branche oder Ihr Geschäftsmodell relevant sind.
Step 2: Define the Scope of Your IT Security Implementation
An effective security implementation requires clear boundaries. Define:
- Assets to Be Secured: This includes data, systems, software, personnel, and processes.
- Organizational Units: Decide which departments or teams will participate.
- Geographical Scope: Account for all offices or facilities, if applicable.
By outlining your scope, you’ll ensure your efforts remain targeted and efficient.
Step 3: Conduct a Risk Assessment
At its core, BSI IT-Grundschutz revolves around understanding and mitigating risks. Conduct a comprehensive risk assessment by:
- Identifying critical assets and their vulnerabilities.
- Mapping potential risks and classifying their probability and impact.
- Identifying current controls in place and any gaps.
This assessment will serve as the backbone of your implementation plan.
Step 4: Select Appropriate Security Controls
Based on your risk analysis, it’s time to choose the security measures that will safeguard your organization. BSI IT-Grundschutz modules provide specific controls for areas like:
- Physical security (e.g., access management).
- Network protection (e.g., firewalls, encryption).
- Personnel training to counter social engineering.
Focus on controls that address high-priority risks, balancing effectiveness with cost.
Step 5: Implement Security Controls
Implementing your selected controls might involve acquiring new tools, updating processes, or providing employee training. Here are some best practices:
- Collaborate with Teams: Ensure every department understands and supports the implementation process.
- Use Automation: Deploy tools that automate repetitive tasks like patch management and vulnerability scanning.
- Track Progress: Keep a record of actions taken, ensuring alignment with your original plan.
Step 6: Monitor and Maintain Security Controls
Cyber threats evolve constantly, so your security measures need regular monitoring and maintenance. BSI IT-Grundschutz emphasizes:
- Continuous Monitoring: Use automated systems to identify real-time vulnerabilities.
- Regular Audits: Perform scheduled evaluations to assess the effectiveness of implemented controls.
- Incident Response Plans: Update your strategies to handle security events proactively.
By following these ongoing practices, you’ll ensure lasting compliance and protection.
Benefits of Implementing BSI IT-Grundschutz
Adopting the BSI IT-Grundschutz framework offers several significant benefits:
- Improved Security Posture: It helps protect sensitive data, critical operations, and customer trust.
- Regulatory Compliance: The framework aligns with GDPR, ISO 27001, and other industry standards.
- Operational Confidence: Teams can work more efficiently, knowing proper security measures are in place.
- Risk Reduction: Identify, mitigate, and proactively manage threats before they escalate.
- Enhanced Reputation: Businesses known for prioritizing security are more likely to attract clients and partners.
IT Security Compliance is Your Competitive Advantage
BSI IT-Grundschutz is far more than a regulatory checkbox; it’s a toolset that helps safeguard your digital infrastructure, strengthen your business resilience, and maintain customer trust. Whether you operate within the government, military, critical infrastructure, or private sector, the framework can make compliance attainable and IT security manageable.
By understanding your specific risks, working through the framework’s steps, and prioritizing continuous improvement, you’ll create a robust security environment that protects your organization today and prepares it for tomorrow’s threats.
Need expert guidance to simplify your IT security implementation? Reach out to a certified consultant or explore tools that integrate BSI IT-Grundschutz frameworks seamlessly into your business operations.

